In part 5 here ,we have downloaded the MDOP 2015 templates ,extracted,copied MBAM 2.5 SP1 .admx and .adml templates to our Domain controller ,Created GPO for workstation OU and deployed it. In this Part 6 of MBAM 2.5 SP1 multi series guide ,we will create collection ,application for MBAM 2.5 SP1 agent and deploy to our Clients and do the bitlocker encryption stuff.
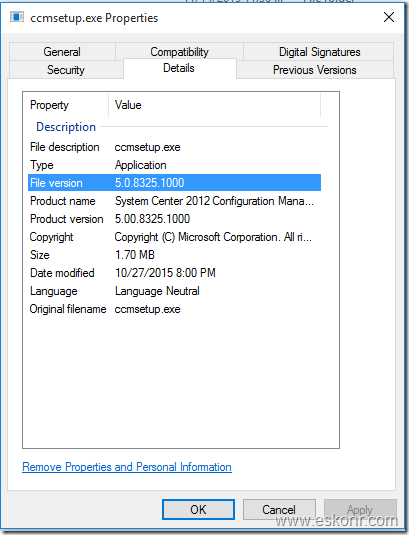
In earlier versions of MBAM ,it usually ships with MSI which can be directly import to SCCM /GPO where as in MBAM 2.5 SP1, a separate MSI is no longer included with the MBAM product. However, you can extract the MSI from the executable file (.exe) that is included with the product.
If you look into the MBAM installer file in MDOP 2015, you will find only 2 .exe files as shown below for X64 ,same applicable to X86 (clientsetup) also.
![image image]()
we will try to extract MbamClientSetup.exe to get .msi and then import into SCCM application deployment method.
The command line to extract .MSI from .exe file is : MBAMClientSetup.exe /extract "D:\MBAMClient\MbamClientSetup" /acceptEula=Yes
MBAMClientSetup.exe : is the actual file trying to extract
D:\MBAMClient\MbamClientSetup: Path to extract MSI
if you don’t want to go with MSI file,can still use .exe file to deploy MBAM Agent using command line: MBAMClientSetup.exe /acceptEula=Yes
Command line installation for MSI: msiexec /i "MSI file name" /qn REBOOT=ReallySuppress
we will now copy the MSI file to our Source folder in SCCM server.
![image image]()
Create collection called MBAM_client_2.5SP1 and add few test computers (windows8 and Windows 10) to it. In my lab,I used following Query based rule to add all workstations with Client Agent=Yes
select * from SMS_R_System where SMS_R_System.OperatingSystemNameandVersion like "%Workstation%" and SMS_R_System.Client = "1"
Lets create Application using this MSI file and deploy to our MBAM_client_2.5SP1 Collection. Create application as you do for other MSI’s .
Edit the deployment type to change the name of the DT (like MBAM Client 2.5 SP1 X64,if deploying 32bit then X86) ,requirements tab to limit this to workstations (win8,Win10 etc) and other properties if needed.
Deploy the application to Distribution point Group/Distribution and deploy to collection.
Login to test PC (windows 8.1/Windows 10) ,check if MBAM Agent 2.5 SP1 is deployed or not.
Demo: Windows 8.1
On physical machines, to do bitlocker encryption,you must have TPM chipset enabled and activated. TPM chipset is hardware based sits on motherboard and does specific functions.More information about TPM and Bitlocker,read https://msdn.microsoft.com/en-us/library/windows/hardware/dn653315(v=vs.85).aspx
Note:while performing the Bitlocker drive encryption on Hyper-V vms, I always keep getting error (will in below guide) “BitLocker Drive Encryption only supports Used Space Only encryption on thin provisioned storage.” so I assume this is known iss as vm’s aren’t supported as per this TechNet article but should work in physical machines without any issue.So in lab,we will try to do bitlocker using manual method instead of doing it via MBAM agent and rest will be managed by MBAM only. I will update this post ,when I find solution.
So in lab,instead of encrypting the the drive using MBAM agent,we use manual method from control panel. This is only step we are by-passing and rest of process is managed by MBAM .
If you are trying this on physical machine that ,it should work good for you without any issues(atleast you will not see above error).
Login to Windows 8.1 PC ,check if the MBAM agent is deployed successfully or not .You can check this from either Software Center or from C:\program files \Microsoft\ MDOP MBAM
After the Agent installed ,next step to check is GPO settings that we have created in part 5 (MBAM 2.5 SP1 Client settings) loaded correctly or not.How do we check if the GPO settings applied correctly or not ?
Open the registry key on windows 8.1 client ,(type regedit from RUN command) ,browse to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE
From below snippet,you can see that ,Configure pre-boot recovery message and URL’s configured via GPO are applied which is new in MBAM 2.5 SP1.
![image image]()
and from HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE\MDOPBitLockerManagement
![image image]()
You can copy the URL from the registry key and check if you can browse to that or not to confirm if Client is able to talk to MBAM server.
We can also check if the Client is able to download the MBAM policies from MBAM server or not using event viewer.s
Location to check Bitlocker encryption and operation issues : Event Viewer – Applications and Services Logs – Microsoft – Windows – MBAM (Admin and Operational)
After this settings applied correctly to our Windows 8.1 client ,you will soon receive a prompt like below.
If you don’t see the prompt,troubleshooting is required, but you can launch the MBAM wizard by running MBAMCLIENTUI.exe from C:\program files\Microsoft\MDOP MBAM (this folder may vary depends on the OS architecture)
In the GPO settings, we have set 0 without any grace period to postpone the bitlocker drive encryption .With this setting,user cannot close this action and must do encryption (But in production this setting may vary).
![image image]()
Enter the password between 8-255 character and click Create Password.
Here is my next screen for bitlocker status:
![image image]()
For some reason,it failed encrypting the disk .What next ? we don’t have any logs like we do for SCCM but as I discussed above,can check the reasons for this failure using event viewer.
Go to Event Viewer – Applications and Services Logs – Microsoft – Windows – MBAM (Admin and Operational)
Check for operational if Client is able to download the policies correctly or not.
![image image]()
From above screen,client is able to pull the download the policies ,next look at Admin section.
![image image]()
So as I discussed earlier in Note,lets do the bitlocker manually .For this,open Control Panel\All Control Panel Items\BitLocker Drive Encryption
![image image]()
Turn on Bitlocker
![image image]()
It will verify the prerequisites and prompt window to enter password:
![image image]()
Enter password between 8-255 characters
![image image]()
For now,we will try to save the file to remote PC (this file consists of Bitlocker recovery key help you to unlock your computer incase you forget the above password).
![image image]()
Accept the default option and click Continue
![image image]()
Restart now
![image image]()
After you restart,it ask for password to continue .if you press ESC,bitlocker encryption process will get cancel and you must do the procedure again.
![image image]()
After you login to the PC,a small window appear on the taskbar with encryption is in progress.
![image image]()
After a while,encryption gets complete and you must see the bitlocker information about this client from your MBAM Server reports.
![image image]()
With this,we have completed the bitlocker encryption on client side using manual method instead of doing it via MBAM Agent.
How to use MBAM 2.5 SP1 selfservice portal to retrieve Bitlocker recovery Key ?
Next ,we will look at MBAM compliance reports using SCCM and also try to recover the bitlocker recovery key incase user forget the password to unlock the computer during the boot process.
Restart the Client PC (8.1 VM) ,it prompt to enter the password
![image image]()
Incase if you forget the Password and want to retrieve the bitlocker recovery key. Press ESC ,it takes you to below screen to enter the recovery Key for this drive.
Note: This recovery key keeps changing every times you press ESC .When you press ESC ,a new recoverykey will be created in the MBAM Recovery and Hardware database.
To retrieve the Bitlocker Recovery Key ,we need to have the first 8 digit of Recovery Key ID (364ACBC6) shown in the below screen and retrieve the recovery Key using self service portal as discussed in part 4.
![image image]()
So launch the selfservice portal on any computer who has enough security permissions to run the selfservice portal and run the URL: http://mbam01.corp.eskonr.com/SelfService
As shown below ,enter the first 8 digit recovery Key ID and select the reason what you are interested in (all these requests will be stored in database for auditing purpose incase you want to check how many times performed like this).
![image image]()
238689-104929-336666-292017-263890-562496-482768-388982
again,this bitlocker is one time usage and not used again and again.Every time when you request for recovery key,it creates new one.
You can also perform the SQL query to get the recovery key instead of going via portal .This recovery key information stored in database (MBAM Recovery and Hardware) table (RecoveryAndHardwareCore.Keys).
Enter the recovery Key which we obtained from above and press Enter
![image image]()
it should allow you to login.
![image image]()
With this ,we have completed the demo on ,how to get Bitlocker recovery key using self service portal.
Next ,we will see the compliance results using SCCM configmgr reports.
Before that ,you must confirm if the hardware and Configuration.mof changes are processed successfully on the server also enabled the inventory for TPM,Bitlocker,MBAMpolicy etc as discussed in part 3 here
Once you are confirmed,lets run the hardware inventory schedule on the client (if you want can’t wait for the default schedule to run) and monitor inventoryagent.log on the client PC.
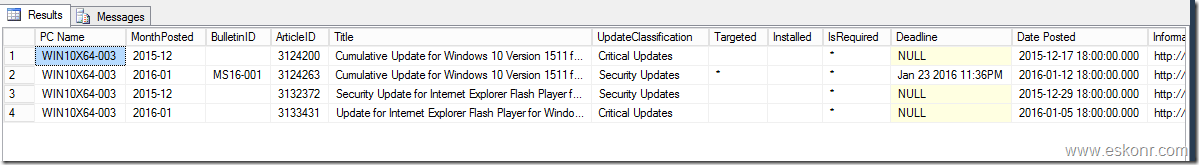
From the log,we mainly interested in changes i.e MBAM policy and Bitlocker as the MBAM reports are mainly depends on these tables/views.
![image image]()
wait for few min for the site server to process this information and update in database.
Run the Configuration manager reports URL http://cm01/Reports/ (my SCCM report server CM01).
![image image]()
I am interested to to know the Bitlocker Enterprise Compliance summary report.
By default,the report select MBAM supported computers but you can select the collection from drop down list.
![image image]()
We have got 1 computer with 100% complaint but this report is missing linked report to know what computer is that .
If you get any error "Error: the 'MBAM Policy' view does not exist" while running the reports, make sure you have at least one client reported the inventory for MBAMPolicy else the report have nothing to present you.
With this,we have completed how to extract MBAM 2.5 SP1 Client agent MSI from EXE ,created application using MSI in SCCM 2012 R2 SP1 ,deployed to collection,did bitlocker manually due to vm support issue ,retrive the bitlocker key using self service portal and finally run the compliance reports using SCCM.
In the next part 7,we will see the new features added to support windows 10 like Customize pre-boot recovery message and URL .
 Powershell script to Detect the Security permissions:
Powershell script to Detect the Security permissions: